Hackers, the Round 2 Results for the Cybersecurity Writing Contest are here! For those who are reading about it for the first time -
Share your cybersecurity stories today! The competition is getting tougher. This month we received some REALLY fantastic entries. So good luck y’all; the bar is high.

The Cybersecurity Writing Contest July 2022 Nominations
We picked all the stories tagged with the #cybersecurity tag on HackerNoon, published in July 2022. As usual, we chose the top stories using 60:30:10 weightage respectively to:
- Number of hours read
- The number of people reached
- The freshness of the content
Here are the top 10 nominations for the second round:
- How to Avoid Credit Card Skimming: 5 Tips to Keep Your Information Safe by @DawoodKMasood
- How To Find Out If A Hacker Has Attacked You by @angfaw9
- What is Credit Card Skimming and How Do You Prevent it? by @turbulence
- How My Mother Got Hacked by a Phishing Attack by @fatman
- Essential OSINT Resources in 2022 by @officercia
- Remembering and Honoring the Cybersecurity Pioneer John McAfee by @nebojsa.todorovic
- This Vulnerability May Allow Hackers to Steal Your Ether by @officercia
- How Secure Are Blockchain Networks Today by @gabrielmanga
- Explaining Info-Sec in Layman's Terms [Part II] by @heydanny
- What is BGP Hijacking and How Do You Prevent It? by @thecloudarchitect
Winners!
The editors then voted for the top stories. Here are the winners for the month of July:
In the first place, we have How To Find Out If A Hacker Has Attacked You by @angfaw9
Congratulations on winning 500 USD!, @angfaw9 :)
Many hackers make a living by redirecting your browser to a link other than the one you want. Unfortunately, to date many of the redirected Internet searches are well hidden from the user through the use of additional proxies, so the bogus results are never returned to alert the user.
How My Mother Got Hacked by a Phishing Attack by @fatman has won the second position!
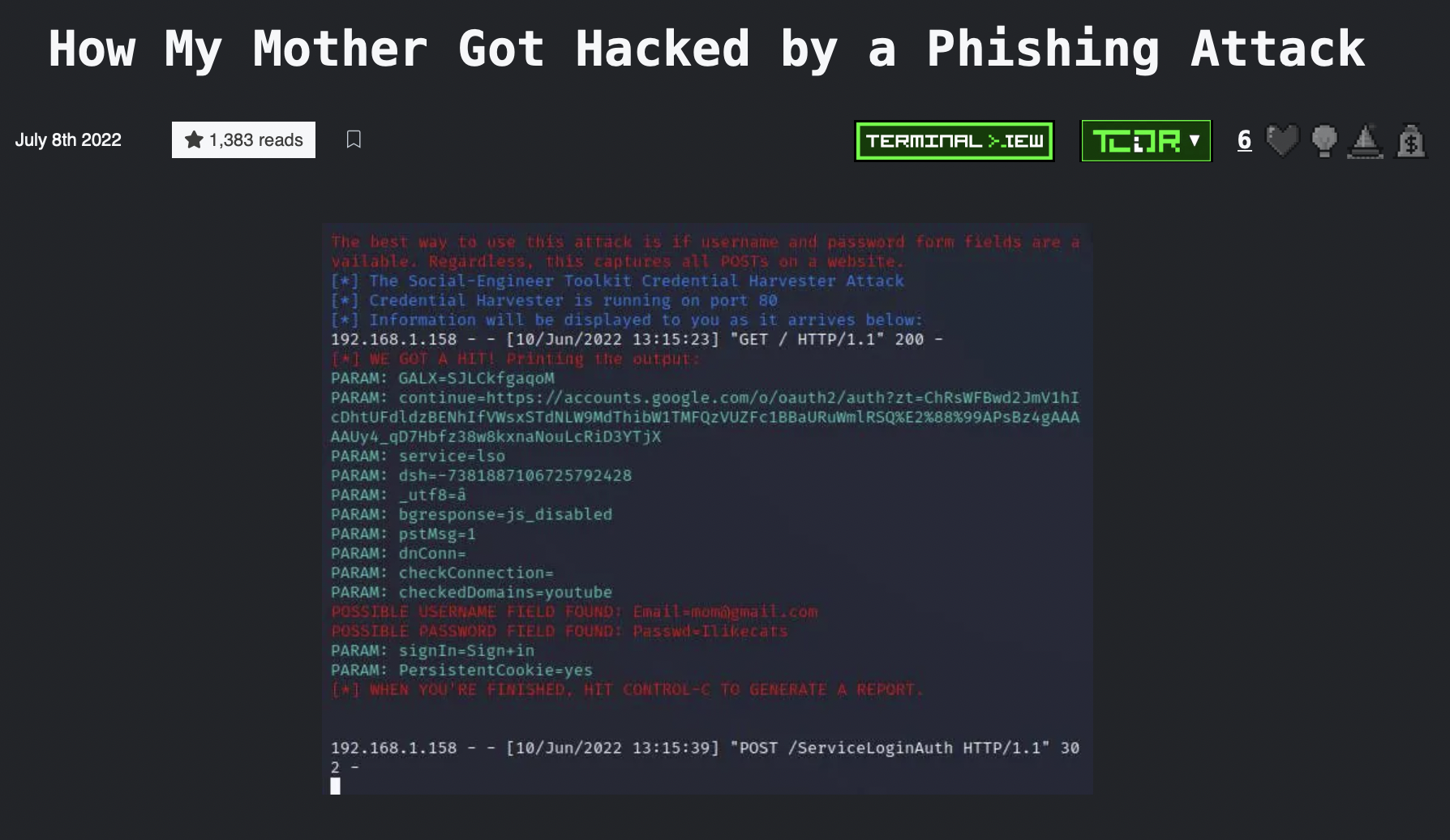
A carefully crafted phishing email lacking typos or bizarre grammar is important to the success of the phishing campaign. The email she received was similar to this one with the subject line: Verify Your Google Account.
The editors enjoyed your story @fatman! You have won 300 USD!
In the third place, we have Remembering and Honoring the Cybersecurity Pioneer John McAfee by @nebojsa.todorovic
The last couple of years, especially the last one, were… Yeah, it’s not easy to come up with the right word(s). We have been totally numbed, haven’t we? Nothing and no one can’t surprise or shock us anymore. How long did the news about John McAfee’s death occupy your thoughts? Long enough to remind us about his controversies, and not long enough to remember his achievements.
Excellent storytelling, @nebojsa.todorovic! You have won 100 USD this month!
The most-read story this month is How to Avoid Credit Card Skimming: 5 Tips to Keep Your Information Safe by @DawoodKMasood with MASSIVE 76,571 reads so far.
Wow, look at those numbers @DawoodKMasood. You’ve won 100 USD.
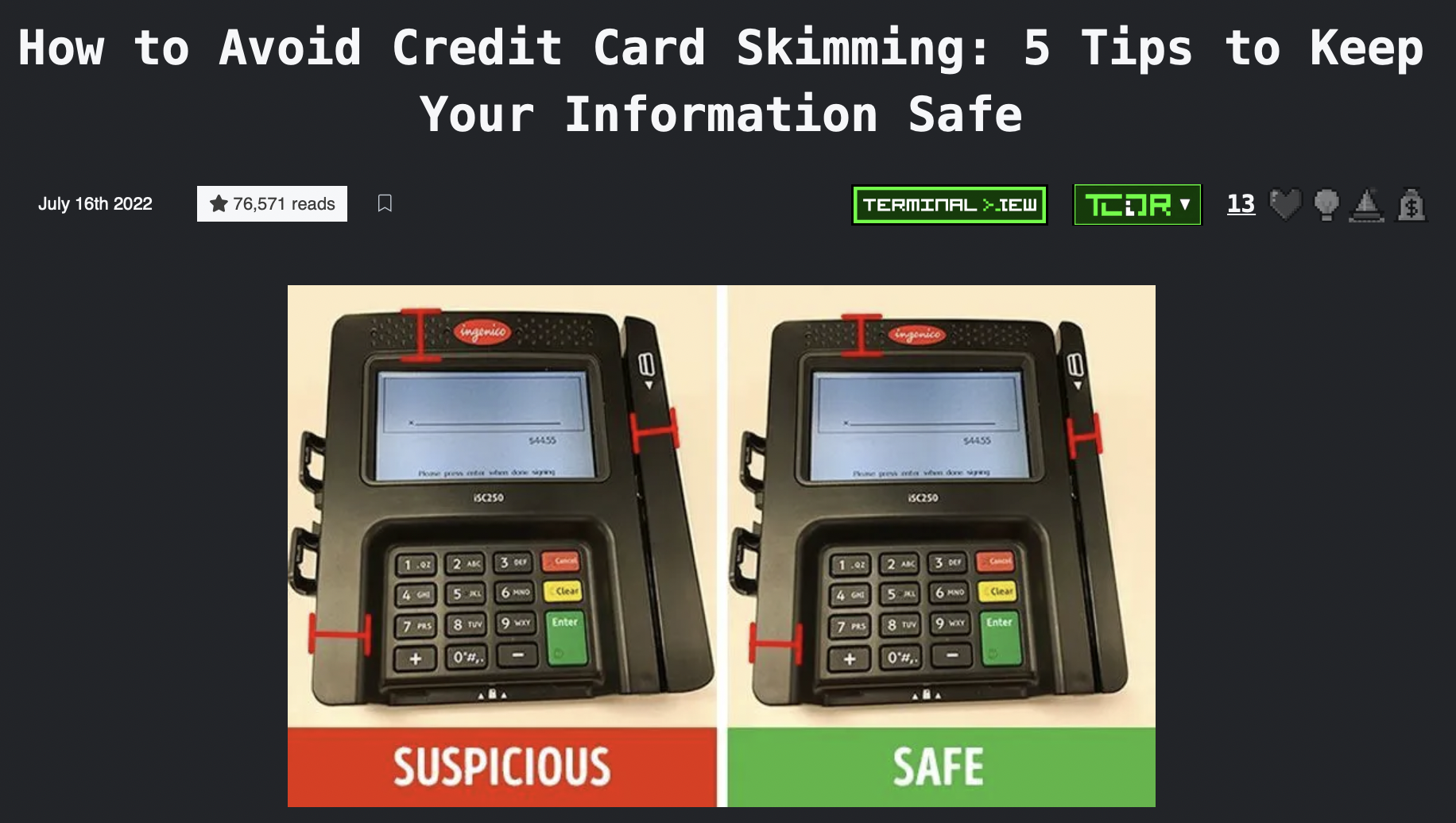
One of the best ways to avoid credit card skimming is to pay attention to your surroundings when you're using your card. If you notice anything suspicious about the credit card reader, don't use it. You should also check your billing statement regularly to make sure that all of the charges are legitimate. Finally, if you're ever in doubt, you can always contact your credit card company to ask about suspicious charges.
Let’s wrap up the announcement! We will contact the winners shortly. Keep an eye on contests.hackernoon.com to see the current and upcoming writing contests!
